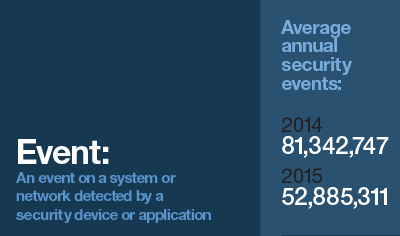
As businesses become increasingly reliant on data and online platforms, they are also becoming increasingly concerned about cybercrime. And they are right to do so. According to IBM’s 2016 Cyber Security Intelligence Index, the average client organisation monitored experienced around 53 million security ‘events’ in the course of 2015, with 1,157 direct ‘attacks’ (defined by the report as “malicious activity that is attempting to collect, disrupt, deny, degrade or destroy information system resources or the information itself”). The five worst-hit industries were, in descending order: healthcare, manufacturing, financial services, government agencies and transportation.
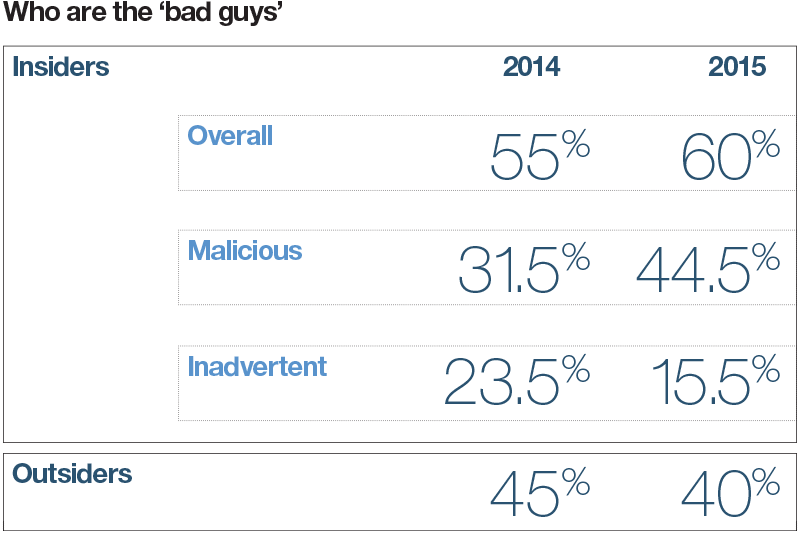
Worryingly, the most likely culprit for your organisation’s next attack is someone you thought you could trust, be it an employee, contractor or consultant. Insider attacks still pose the most significant single thereat to businesses around the world, accounting for 60 percent of all attacks.


The majority of these breaches involve the use of viruses, spyware and malware – all methods that, given the right technology, can be prevented. As the threat of cyberattacks continues, businesses must take concrete steps to protect the integrity of their IT infrastructure.
Fortunately, leading firms are now waking up to the threat. According to the UK Government’s Cyber Governance Health Check, half of FTSE 350 companies regard the risk of cyberattack as the key threat facing their business. This is an increase of 29 percent on reported concerns in 2014.
Firms must take every possible step to safeguard against their vulnerabilities. Each business’ needs will be different, and their attackers agendas varied. As the authors of the IBM report pointed out: “While financial gain is still a powerful motivator for cyber criminals, it’s by no means the only one. Last year’s attackers branched out in a big way – inflicting physical damage, stealing intellectual property and lodging political protests.” Traditional security defences will not stand up to this onslaught, particularly as disruptive technologies bring new and unpredictable vulnerabilities.
Although the figures are startling, the news is not all bad. IBM reported its client business had seen a significant reduction in events and attacks from the previous year, while the rate of discovery had increased, demonstrating that – with the right support – businesses can still turn the tide.
Brexit bother In 2015, the European Commission’s arm concerning banking and finance released its newest directive covering online payment services. Known as PSD2, it will bring a number of changes to the way online payment services for businesses operate within the EU. And the ramifications could be huge.
Under the directive, online retailers will be able to ask consumers for permission to use their bank details, meaning retailers could receive payments directly from the customer’s account. Instead of payment intermediaries, transactions will be carried out via APIs. The new regulation will also result in the introduction of ‘account information service providers’, or AISPs, which will allow users to view all of their banking information – even if dispersed between different accounts – through one single portal.
While this added convenience will be a boon to consumers, it will be a bit more worrying for banks, who will need to decide what role they can play in this new payments ecosystem. It could be an opportunity for financial institutions to reinvent themselves, but that would be very expensive at a time when their existing revenue streams will be reduced and a whole new wave of fintech competitors will be entering the market.
The outcome of the directive will be particularly unclear for businesses operating in the UK, which voted to leave the EU back in June 2016 – particularly as, at the time of writing, the exact nature of the country’s exit remains unclear. If the UK leaves the European Union but remains a part of the European Economic Area, the country will still be subject to many single market regulations, and the PSD2 regulation changes will probably be implemented along the same lines as if the UK were still a member of the EU (assuming it does not exercise its right within the EEA to unilaterally place a stop break on the policy). Indeed, implementation of the new regulations should actually be easier in the UK than in many full member states, as the country is already ahead in terms of data sharing due to the UK Open Data Initiative.